Yesterday's iOS 7.0.6 update provided a fix for an SSL connection verification issue, which turned out to be a major security flaw in the operating system. In a support document, Apple noted the patch repaired a specific vulnerability that could allow an attacker with a "privileged network position" to capture or modify data protected by SSL/TLS.
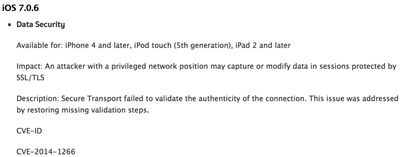
In other words, iOS was vulnerable to a man-in-the-middle attack where an attacker could pose as a trusted website to intercept communications, acquiring sensitive information such as login credentials and passwords, or injecting harmful malware.
According to security firm CrowdStrike, OS X may be vulnerable as well, because it exhibits the same authentication flaw. OS X users are open to an attack on any shared wired or wireless network as SSL/TLS verification routines can be bypassed.
To pull off the attack an adversary has to be able to Man-in-The-Middle (MitM) network connections, which can be done if they are present on the same wired or wireless network as the victim. Due to a flaw in authentication logic on iOS and OS X platforms, an attacker can bypass SSL/TLS verification routines upon the initial connection handshake.
This enables an adversary to masquerade as coming from a trusted remote endpoint, such as your favorite webmail provider and perform full interception of encrypted traffic between you and the destination server, as well as give them a capability to modify the data in flight (such as deliver exploits to take control of your system).
The bug, which has been detailed by Google software engineer Adam Langley, may have been introduced in OS X 10.9. According to Hacker News users, it remains unclear whether the issue is fixed with the latest version of the software, OS X 10.9.2, which is currently only available for developers. Users can check whether or not their computers are affected by the vulnerability by visiting gotofail.com in Safari.

It is likely that Apple plans to release a fix for OS X in the near future to repair the vulnerability, but in the meantime, CrowdStrike recommends avoiding untrusted WiFi networks while traveling. The site also recommends an immediate update to iOS 7.0.6 for users who have not yet installed the newest version of the operating system on their iOS devices.
Update: Apple has told Reuters that it is aware of the issue and has a software fix that will be released "very soon."





















Top Rated Comments
:apple:
This has nothing to do with a particular browser. It's a flaw in the core OS X system security framework that software use to encrypt https (and other) connections.
The fact that Apple made iOS it's first priority is very revealing, they could have made it their highest priority to fix both iOS & OS X concurrently.
Furthermore, it reveals how sloppy they're getting. It should have been caught before it was shipped. One minute they patronize the masses, boasting how much they care about their customers, then they pull a stunt like this.
Microsoft wouldn't allow this to go ignored as long as Apple has.
Here's more:
http://www.zdnet.com/apple-and-the-ssltls-bug-open-questions-7000026628/